University of Redlands Emergency Alert System
Alert Received: . For more information, visit: https://www.redlands.edu/alert/
University of Redlands
- Home
- Information Security Office
- You Have Been Phished
YOU'VE BEEN PHISHED
Unfortunately, you became a victim of a simulated attack and typed sensitive information into a deceptive website as instructed in the phishing simulation email message.
Please take a few moments to review these safety recommendations to stay out of danger in the future.
How to spot a phishing email
Cybercriminals have gotten clever in how they design the emails they send out to make them look legitimate. But phishing emails often have the following characteristics:
• Ask you for personal information, such as your username and password, either by replying to the email or clicking on a link that takes you to a site where you’re asked to input the information. IMPORTANT: No one at our University will ever ask you for your password
• Look like they come from someone you know - Don’t trust the display name – Look at the email address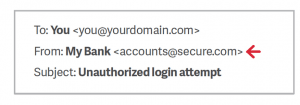 • Contain email addresses that don’t match between the header and the body, are misspelled (like @gmaill.com), or have unusual formats (@redlands-fakesite.com)
• Contain email addresses that don’t match between the header and the body, are misspelled (like @gmaill.com), or have unusual formats (@redlands-fakesite.com)
• Have links or email addresses that show a different destination if you hover over them
• Contain poor spelling and grammar
• Try to make you panic or create a sense of urgency about responding
• Include threats or dire consequences if you don't act quickly
• Seem too good to be true
• Ask you to send money or purchase gift cards
• Ask you to open an attachment or shared a document you may or may not be expecting
• Ask to bypass policy/procedures or do something you wouldn’t normally do
• Ask you not to tell anyone
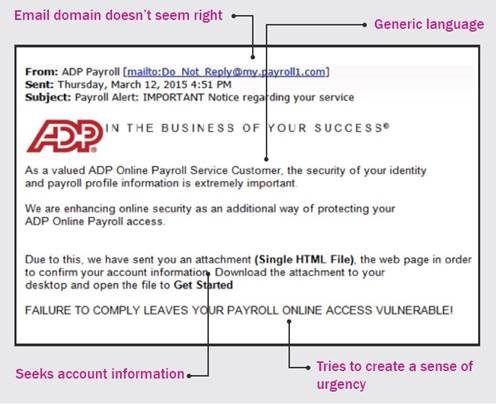
Here is an example of a phishing email:
How to read a URL (Uniform Resource Locater) address
e.g https://www.redlands.edu/a-z-directory/?utm_medium=redlands&utm_source=gnav&utm_content=quick
URLs can be very long and complicated but don’t be intimidated. Reading them is not as hard as it looks and most of the URL can be ignored.
Fake URLs are obvious if you know how to read them.
The simple secret
Now that you’ve found the domain name, how do you know it is not fake?
Excellent video with more details on how to spot fake URLs (12:20 minutes).
https://www.youtube.com/watch?v=TxHdLXi6heY
What you should do if you get a suspicious email

If you suspect that an email is a phishing email or scam:
• Do not open any links or attachments in the email
• Do not respond to requests for information or action
• Report It – abuse@redlands.edu and click on “Report Message” in Microsoft Outlook
• If you’ve already opened a link or attachment, immediately call Technology Support Services – tech_support@redlands.edu or 909-748-8299